Cybercriminals are a wily bunch and the techniques they employ to lure victims to a website or click a link evolve constantly.
With that having been said, there are some common techniques used that are worth taking note of just in case you run into them during the course of your work routine.
To be clear, the following schemes are specifically as regards business email compromise, an aspect of cybercrime that Kaspersky says is on the rise.
“To execute BEC attacks, cybercriminals always carefully harvest data about their victim and then use it to build trust. Some of these attacks are possible because cybercriminals can easily find names and job positions of employees, their exact locations, dates of holidays, lists of contacts and more in open access. Fraudsters generally use a wide range of techniques and methods of social engineering to gain a victim’s confidence and commit malicious operations. That is why we encourage users to be careful at work,” explains head of content filtering methods research at Kaspersky, Alexey Marchenko.
The first scheme Kaspersky highlights is something it calls CEO Fraud. This is where a cybercriminal will send an email posing as a more senior colleague. Here, a cybercriminal will attempt to extract information from the target using a dummy account that looks legitimate.
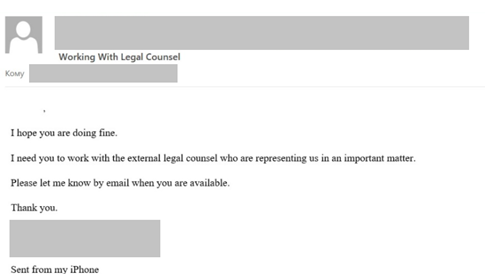
Next up is the Fake Payroll Change scheme. This scheme targets the accounting department and tries to get an employee to change the salary details of another employee. As you might suspect, if this scheme is successful it can cause massive issues for an employer and employee.
In both of the above examples it’s vital that employees contact a senior colleague who can confirm or refute the request sent via email. We’d go so far as to say that this contact shouldn’t happen over email as the colleague’s email could be compromised.
Pick up the phone, send a text message, just make sure that the person emailing you is who they say they are.
Finally, the Fake Invoice scheme remains a faithful method of compromise. Here, a criminal will pretend to be a supplier complaining about the delayed payment of an invoice, if the employee falls prey to this scheme they could potentially be sending funds to a cybercriminal.
As we mentioned, these are just two methods of compromise and cybercriminals are constantly searching for new ways to lure businesses into their traps.
While one could spend millions on security systems, if an employee isn’t trained to identify potential risks, cybercriminals are effectively able to circumvent protections.
Cybersecurity training works and if it can help firms like Capitec, it can help yours.
[Image – CC 0 Pixabay]

