- Cybersecurity firms including Group-IB and Kaspersky have noted an alarming uptick in the amount of data grabbed by info-stealers.
- This malware captures your credentials as you key them into websites and stores them so that cybercriminals can sell those credentials on the dark web.
- Info-stealers have proven to be rather popular for capturing credentials on AI platforms.
Picture this scenario. It’s payday weekend and you decide to meet up with your mates only to find that your bank account has been drained. Upon chatting to the bank you discover that your username and password were used to log in and transfer your money to an account you don’t recognise.
One of the ways modern cybercriminals grab your credentials is through the use of malware known as an info-stealer. The first example of an info-stealer was seen in 2006 when the Trojan ZeuS sought out the credentials of online banking services after being installed on a target device. This malware sits on a computer and secretly logs usernames and passwords as you type them into your browser or elsewhere on your computer.
These logs can then be used by the attacker or sold on hacker forums to other cybercriminals.
Worryingly, there appears to be an upward trend as regards the use of info stealers. In the Middle East and Africa region, Group-IB reports that there has been a 52 percent increase in the number of unique infected hosts. These hosts have had their logs published to underground clouds of logs (UCLs). UCLs are special services where ne’er-do-wells publish compromised credentials and other confidential information.
The cybersecurity firm also notes a 58 percent increase in underground markets where cybercriminals sell illicit wares.
According to Kaspersky, prime targets for cybercriminals include generative artificial intelligence platforms.
“Credentials from various AI services – image editing, translation, text tuning, chatbots, to voice generators – are being compromised due to their growing popularity. Over the past three years, for example, approximately 1,160,000 application users’ credentials (logins and passwords) from AI-powered online graphic design tool Canva were compromised with data-stealing malware. Kaspersky Digital Footprint Intelligence data showed these credentials surfaced on the dark web forums and shadowy Telegram channels. Another popular AI writing assistant, Grammarly, had around 839,000 user credentials stolen between 2021 and 2023,” Kaspersky told Hypertext via email.
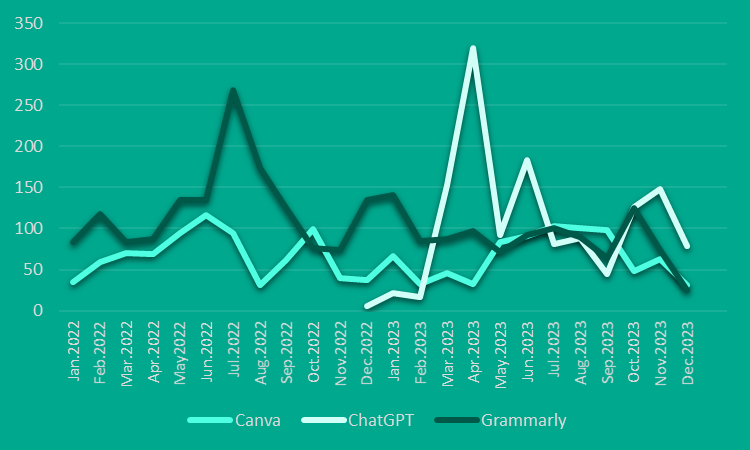
Note that the figures cited by Kaspersky might include duplicates as cybercriminals often reuse previously compromised data.
These credentials can be used for all manner of ills or, as mentioned previously, sold to other crims.
With the above in mind, as regards business owners, it has become vital to employ dark web monitoring to detect whether credentials obtained from info-stealers are being sold to cybercriminals.
For individuals, a robust security solution is important. While Microsoft Security does well to guard against most threats, we recommend using a third-party solution on top of Microsoft’s native product. A solution that monitors the dark web for your credentials is a great feature to be on the look out for.
[Image – Mohamed Hassan from Pixabay]

