While many of us occupy ourselves by trading currencies, assets, trading cards and other valuable items, cybercriminals trade in data. With data, cybercriminals can unlock other doors and when that data comes from a company, those doors can lead to illicit gains.
While data breaches and theft from big firms often grab headlines, cybercriminals also target small and medium enterprises (SME). This makes sense as from a tactical point of view, there are more small businesses than there are large enterprises. According to the World Bank, 90 percent of businesses are classified as SMEs. That’s a massive playground for cybercriminals to run around in.
What is concerning is that SMEs don’t appear to be taking the threat of cybercrime seriously.
In its 2024 Threat Report, Sophos highlighted the digital dangers SMEs face as well as how prevalent attacks are on smaller businesses.
The cybersecurity firm says that in 2023, 75 percent of customer incident response cases handed by its X-Ops Incident Response service, were from small businesses.
Analysis data collected from these cases, Sophos noted several trends. The most prevalent was the use of malware designed to steal information or infostealers.
This malware can collect passwords and log keystrokes sending them to a remote database.
Cybercriminals collate this data and then sell it off to the highest bidder. With business credentials, cybercriminals can often gain access to other services and even other parts of the business. According to Sophos, 90 percent of cyberattacks reported to it in 2023 involved data or credential theft.
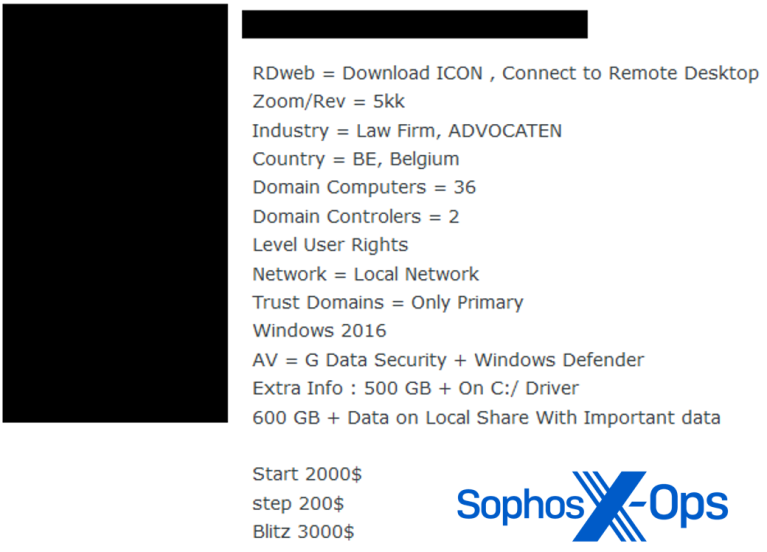
“The value of ‘data,’ as currency has increased exponentially among cybercriminals, and this is particularly true for SMEs, which tend to use one service or software application, per function, for their entire operation.
For example, let’s say attackers deploy an infostealer on their target’s network to steal credentials and then get hold of the password for the company’s accounting software. Attackers could then gain access to the targeted company’s financials and have the ability to funnel funds into their own accounts,” Christopher Budd, director of Sophos X-Ops research at Sophos said in a statement.
Lockbit stepped up
Despite infostealers rising in popularity among cybercriminals, ransomware is still used and remains a notable threat to SMEs.
The ransomware du jour for 2023 was created by the LockBit ransomware gang. Thankfully, the gang’s main servers were seized and two men were arrested for connections to the attacks.
The gang’s ransomware was responsible for the majority – 27.59 percent – of ransomware attacks investigated by Sophos last year with ransomware from Akira (15.52 percent) and BlackCat (13.79 percent) following close behind.
Sophos notes that as 2023 went on it noted an increase in the number of remote execution of ransomware using unprotected devices on a firm’s network. Servers, personal devices, internet of things devices even printers can be compromised and spread ransomware and other ills to other devices on the network. As many of these devices have unchanged default passwords that can easily be found online or cracked, they are easy pickings for cybercriminals looking to extort a business.
The human touch is still effective
Social engineering is still a major threat as is business email compromise per the Sophos report.
The ability for cybercriminals to manipulate a target into handing over information they ordinarily wouldn’t have only been enhanced by large language models. However, Sophos notes that crooks have become incredibly brazen in their tactics going so far as to call targets.
“In the past year, Sophos’ messaging security team came across a slew of new social engineering tricks and techniques designed to evade conventional email controls. Messages in which the attacker emails an attachment or link out of the blue are now passé: The more effective spammers are more likely to strike up a conversation first, then move in for the kill in follow-up emails,” the firm writes.
“We observed this methodology in attacks in which spammers posing as delivery service workers called enterprise customers on the phone and asked them to open a weaponized email. We also saw spammers initially email a solicitation for business or complaint, in attacks targeting a variety of industries in 2023, followed by a link to download a disguised, weaponized file after the business responded to the first email,” it added.
The firm adds that spammers are also finding ways around email protections. This can take the form of replacing text with images including images that look like invoices. These invoices can contain numbers the target is prompted to call. This may instil confidence in an employee that the invoice is legitimate or lure them into unintentionally downloading malware.
These are just a sample of the threats SMEs faced in 2023 and you can be assured that the tactics and threats will only become more severe in 2024.
No matter how small your business is, cybersecurity should be a vital part of your operations precisely because it is small. A large enterprise can generally survive a cybersecurity incident but could the same be said for a small business? We don’t think so.
[Image – Satheesh Sankaran from Pixabay]

