- Cybercriminals are tricking folks into downloading malware using fake CAPTCHA tests and fake Google Chrome error messages.
- The malware steals information from the user’s PC including cryptocurrency-related files, cookies, and password manager data.
- Users are advised to deploy a robust security solution to avoid running across this malware campaign.
On your journey through the internet you’re bound to run across a Completely Automated Public Turing test to tell Computers and Humans Apart, commonly known as a CAPTCHA test.
While fairly innocuous, Kaspersky now reports that this mainstay of the internet is now being exploited in a new campaign. The cybersecurity firm says that while browsing the web, users may encounter invisible ads that cover the entirety of a web page. When clicked, the user is directed to a fake CAPTCHA test or a fake Chrome error message. In both instances the user is asked to download a file which is actually an info-stealer.
Between September and October, Kaspersky’s telemetry has recorded 140 000 encounters with these adverts with 20 000 of those encounters seeing a user clicking the hidden link. The encounters were recorded in Latin America, Africa, the Middle East and Asia.
“Attackers bought some advertising slots, and if a user gets to see this ad and click on it, they are redirected to malicious resources, which is a common attack tactic. The new wave of this campaign involves a significantly expanded distribution network and the introduction of a new attack scenario that reaches more victims. Now users can be lured away by either a fake CAPTCHA prompt or a Chrome webpage error message, falling victim to a stealer with new functionalities. Corporate users and individuals should exercise caution and think critically before following any suspicious prompts that they see online,” comments Vasily Kolesnikov, security expert at Kaspersky.
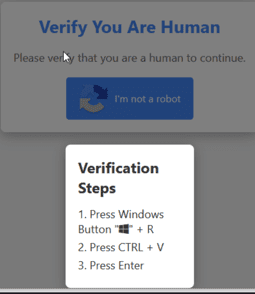
In the example Kaspersky provided above, the user is directed to hit the Windows Key and R together. This opens the Run dialog box for Windows. The text the user copies will download a file from the internet likely without the user realising. The file downloaded is Lumma stealer. Once downloaded, Lumma scans a computer for cryptocurrency-related files, cookies, and password manager data.
Bizarrely, the malware would also visit a number of ecommerce platforms to boost the traffic of those platforms. Kaspersky says that the CAPTCHA attack targeted gamers visiting gaming websites.
The fake Google Chrome error goes further, directing users to open Powershell with Administrator privileges. They are then told to copy and paste a text string which “updates” the computer. Again, this is just a tactic to get a user to run a malicious script that leaves them vulnerable.
“Kaspersky discovered that the new wave of the attack targets not only gamers, but other groups, and is distributed through file-sharing services, web applications, bookmaker portals, adult content pages, anime communities, and other channels. The attackers also use the Amadey Trojan in this wave of the attack – like Lumma, it steals credentials from popular browsers and cryptocurrency wallets, but it can also take screenshots, obtain credentials for remote access services, and download a remote access tool to the victim’s device, allowing the attackers to gain full access,” writes Kaspersky.
The company says that the best way to protect yourself from this sort of attack is by using a robust, up-to-date security solution.
[Image – Janos Perian from Pixabay]

