While WhatsApp may have looked on with envy as Telegram became the most downloaded app in January 2021, Telegram may have a massive problem on its hands.
That problem is cybercriminals using Telegram as a ready to go command and control server for malware. While this has been happening since as far back as 2017, according to Check Point, given Telegram’s rise in popularity it’s worth highlighting.
Why Telegram though?
The platform has a number of features which are attractive to cybercriminals. For one, it is a legitimate service which isn’t blocked by anti-virus engines or network management tools so traffic to a C&C server hosted on Telegram likely won’t raise alarms.
As Telegram works on mobile, it’s also easy for attackers to infect targets when they aren’t in front of their PC.
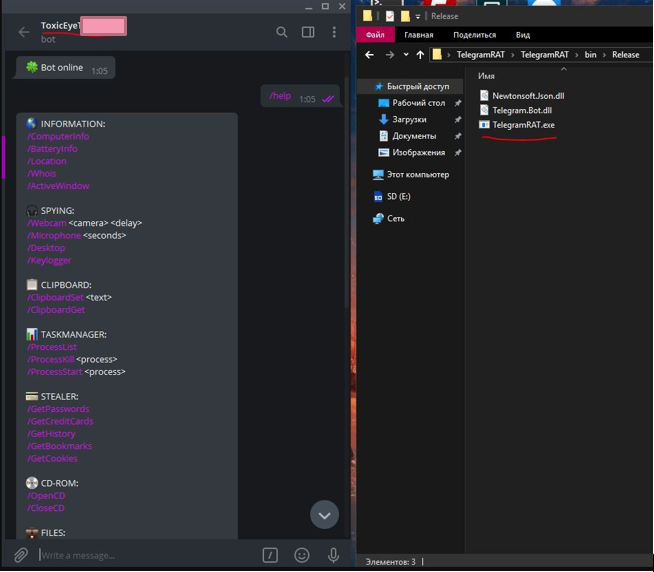
Over the last few months Check Point has discovered a remote access trojan (RAT) it has called ToxicEye. The RAT has been used in over 130 attacks and is spread via a malicious .exe delivered via phishing attacks.
ToxicEye can perform a number of exploits including:
- data theft
- deleting or transferring files
- kill processes on a target PC
- hijack the microphone and camera to record video and audio
- encrypt files for a ransom
An example of the C&C server bot cybercriminals use, “The attacker first creates a Telegram account and a Telegram ‘bot.’ A Telegram bot account is a special remote account with which users can interact by Telegram chat or by adding them to Telegram groups, or by sending requests directly from the input field by typing the bot’s Telegram username and a query,” Check Point explains.
This bot is then embedded into the ToxicEye configuration file and any target can then be attacked using the bot.
Check Point’s advice to users is to search for a folder in C:\Users called ToxicEye, if you discover this file you should contact your IT department or, if you’re at home, scrub the file from your system.
For IT teams the firm advises that you be on the look out for traffic heading to Telegram, if Telegram isn’t used in the organisation this might be an indicator of compromise. Of course, regular people use Telegram so false positives are bound to happen.
It goes without saying that you should be cautious of emails that look suspicious and don’t download files you aren’t expecting or that look like one thing but are actually another.
It’s unclear whether Telegram is aware its platform is being used this way and whether it intends to do anything about this. We suspect the platform will crackdown on this behaviour before too long, or rather we hope that’s the case.
[Image – CC 0 Pixabay]