Over the last few weeks a new name has been uttered by professionals and researchers in the cybersecurity space. That name is LAPSUS$ and if the group’s claims are legitimate – which they increasingly look to be – we have a massive problem on our hands.
On Tuesday afternoon Okta, which provides authentication services, revealed that it had not been breached, but a customer support engineer who works for a third party had been compromised. The compromise allowed LAPSUS$ to see some customer information but the access was limited due to the limited access support engineers at Okta have, according to the firm.
“Following the completion of the service provider’s investigation, we received a report from the forensics firm this week. The report highlighted that there was a five-day window of time between January 16-21, 2022, where an attacker had access to a support engineer’s laptop. This is consistent with the screenshots that we became aware of yesterday,” writes chief security officer at Okta, David Bradbury.
“The potential impact to Okta customers is limited to the access that support engineers have. These engineers are unable to create or delete users, or download customer databases. Support engineers do have access to limited data – for example, Jira tickets and lists of users – that were seen in the screenshots. Support engineers are also able to facilitate the resetting of passwords and multi-factor authentication factors for users, but are unable to obtain those passwords,” the CSO added.
The firm says that approximately 2.5 percent of its customers were potentially impacted by this compromise and those customers will be contacted.
However, LAPSUS$ claims to have had greater access than what Bradbury states. In its Telegram channel, LAPSUS$ claimed to have had Superuser access to Okta’s systems for two months. The group also claims it had access to a thin client (a computer which accesses a central server rather than a local hard drive) not a laptop and goes on to claim that Okta was storing AWS keys in Slack.
While Bradbury says that LAPSUS$ was unsuccessful in its compromise, that’s not what LAPSUS$ says.
“I’m STILL unsure how its a unsuccessful attempt? Logged in to superuser portal with the ability to reset the Password and MFA of ~95% of clients isn’t successful,” the group wrote.
Microsoft also fell foul of LAPSUS$ with the group claiming to have made off with some 37GB of data apparently containing source code – or parts thereof – for Bing and Cortana.
The software giant detailed how LAPSUS$ operates, or rather, Microsoft’s best guess (driven by extensive research of course) at how the group operates in an extensive blog.
The modus operandi for LAPSUS$ appears to be centred on compromising an employee at a firm. This is done through phishing, purchasing stolen credentials or straight up recruiting disgruntled employees via Telegram.
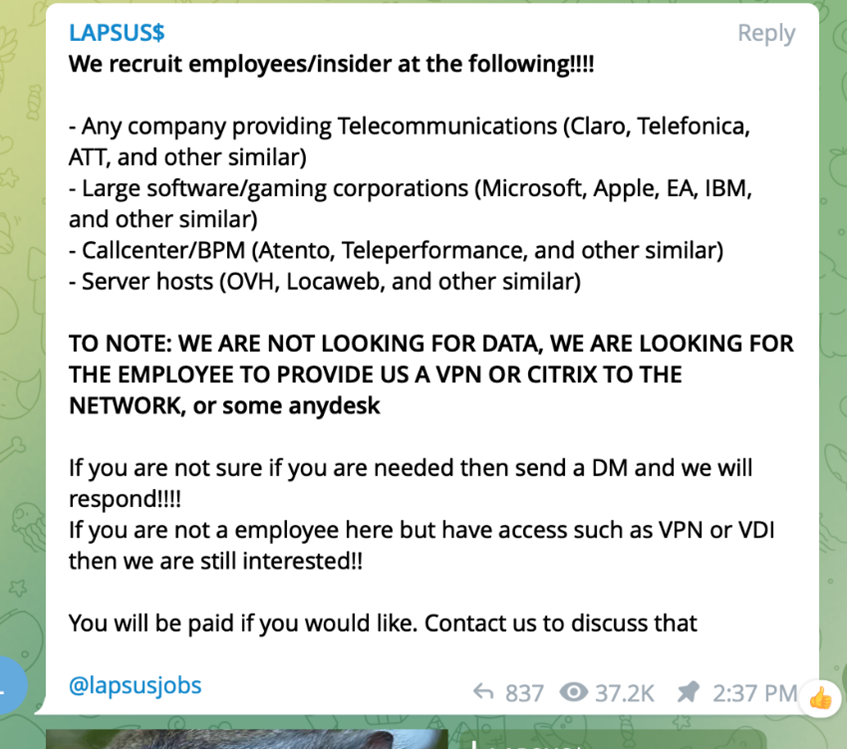
While Okta says that a third-party customer support engineer was the only person who was compromised, that isn’t how LAPSUS$ appears to work. In fact, we’d go so far as to say that any cybercrime group worth their weight in salt isn’t stopping after they compromise a support staffer. Note, Microsoft refers to LAPSUS$ as DEV-0537.
“In some cases, DEV-0537 first targeted and compromised an individual’s personal or private (non-work-related) accounts giving them access to then look for additional credentials that could be used to gain access to corporate systems. Given that employees typically use these personal accounts or numbers as their second-factor authentication or password recovery, the group would often use this access to reset passwords and complete account recovery actions,” the Redmond-based software firm wrote.
Further to this, Microsoft reports that LAPSUS$ connects to a compromised organisation’s VPN which allows them to move through the organisation’s systems without a hassle. The group is also known to perform SIM-swaps to access a target’s phone number just in-case they use mobile authentication systems.
Frankly, LAPSUS$ doesn’t look like the sort of threat group that will walk away after compromising a single notebook and grabbing a few screenshots and it isn’t.
In its research, Microsoft claims that LAPSUS$ purposefully deletes resources such as VMWare, vSphere/ESX and others to trigger an organisation’s incident and crisis response process.
“The actor has been observed then joining the organization’s crisis communication calls and internal discussion boards (Slack, Teams, conference calls, and others) to understand the incident response workflow and their corresponding response. It is assessed this provides DEV-0537 insight into the victim’s state of mind, their knowledge of the intrusion, and a venue to initiate extortion demands. Notably, DEV-0537 has been observed joining incident response bridges within targeted organizations responding to destructive actions. In some cases, DEV-0537 has extorted victims to prevent the release of stolen data, and in others, no extortion attempt was made and DEV-0537 publicly leaked the data they stole,” Microsoft explained.
The group has also claimed responsibility for breaches at Nvidia and Samsung. As regards Nvidia, the group reportedly stole two code signing certificates which allows LAPSUS$ to sign malware in hopes it evades security solutions. Samsung had 190GB of sensitive data published online following the LAPSUS$ breach.
According to this report from Wired, LAPSUS$ started off targeting organisations such as Brazil’s ministry of health, Portuguese media giant Impresa, Claro and others before moving to other targets.
The one “good” thing about LAPSUS$ is that it doesn’t appear to focused on spreading ransomware with its preferred methods being intrusion, exfiltration of data, extortion and finally – in some cases – distribution of data it exfiltrated.
Its actions have been described as erratic and unusual but it’s becoming increasingly clear that LAPSUS$ isn’t flying by the seat of its pants.
As such, businesses are advised to batten down the hatches, enable multi-factor authentication, use strong passwords and avoid using SMS as an authentication method.
We don’t think this will be the last time we hear about LAPSUS$ and we hope that all organisations take note of how badly firms such as Microsoft, Okta and others have been affected by the threat group’s actions.
[Image – CC 0 Pixabay]

